Configure oAuth2 in SAP System
Step 1. In the SAP system, go to SAML2 transaction and make sure that the local provider is enabled. If it is not done, configure according to standard SAP documentation.
NOTE: If several SAP clients are configured, the Local Provider Name in transaction SAML2 must be set to: https://<hostname>:<port>, otherwise, it might cause issues once non-default client should be accessed. Changing the Local Provider Name in SAML2 does not require any changes or XML re-imports on the Azure AD side.
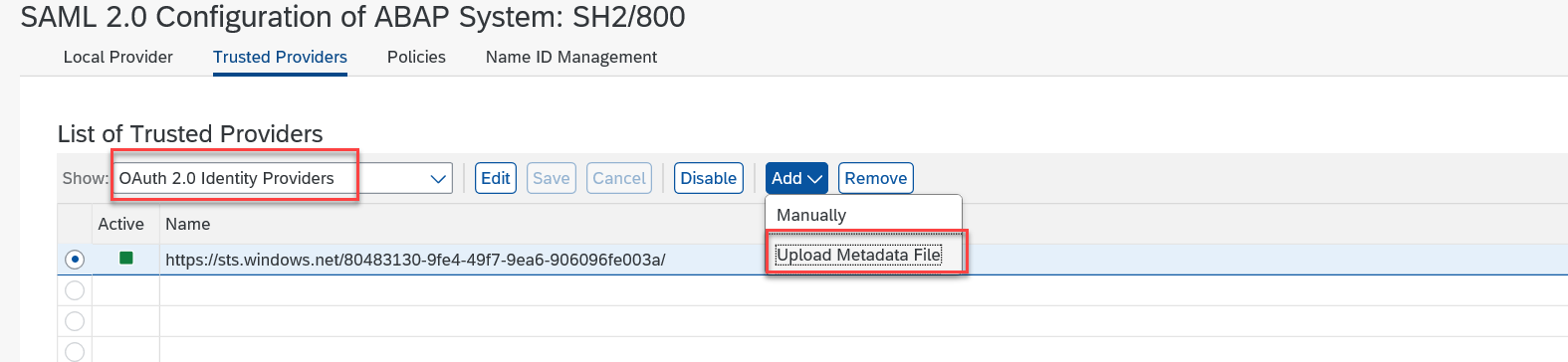
Step 2. Open the Trusted Providers tab and select oAuth Identity Providers. Create a new one using the file and certificate downloaded in Create Azure AD Enterprise Application for SAP Backend
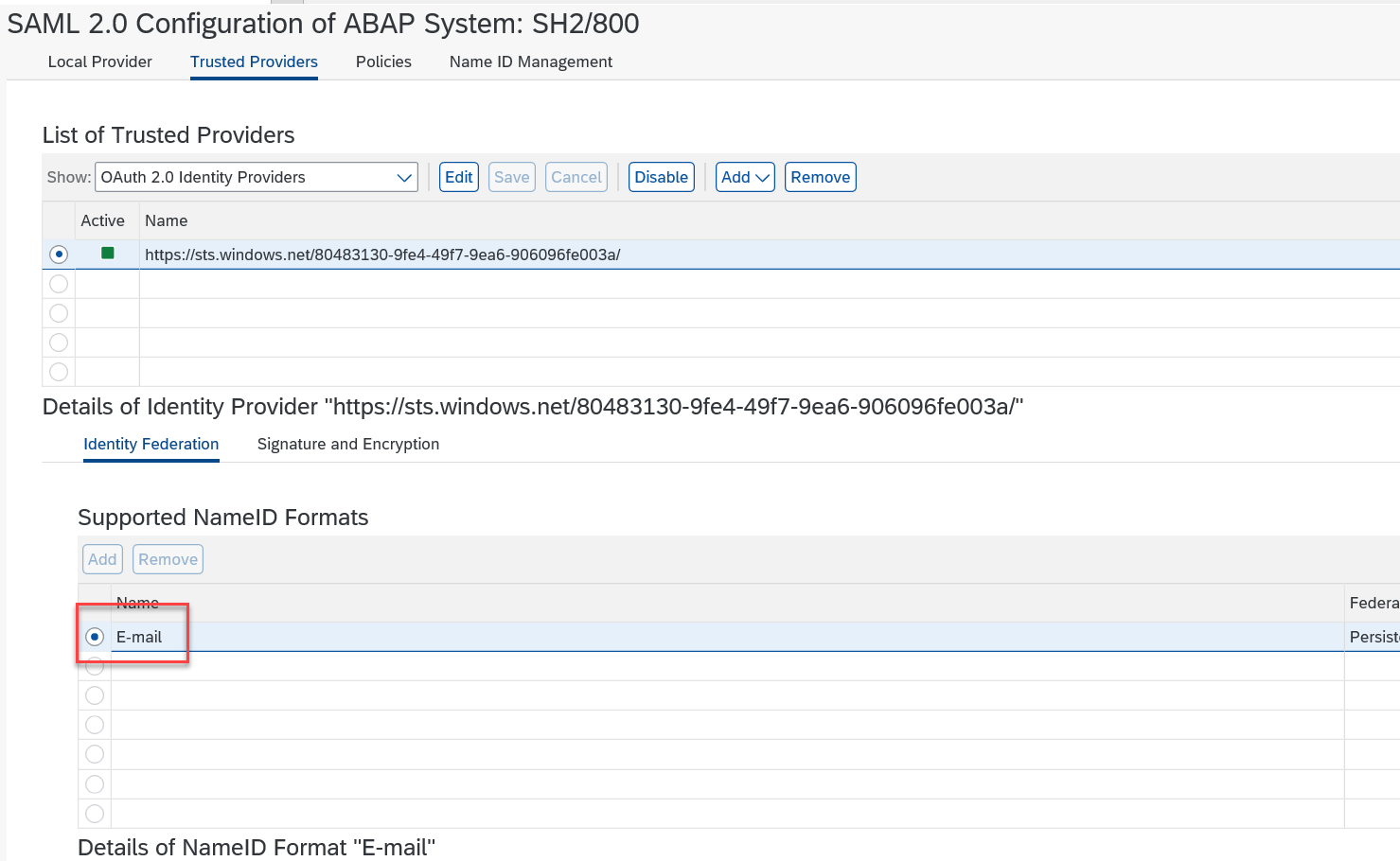
Then add the email as NameID format and activate the service provider.
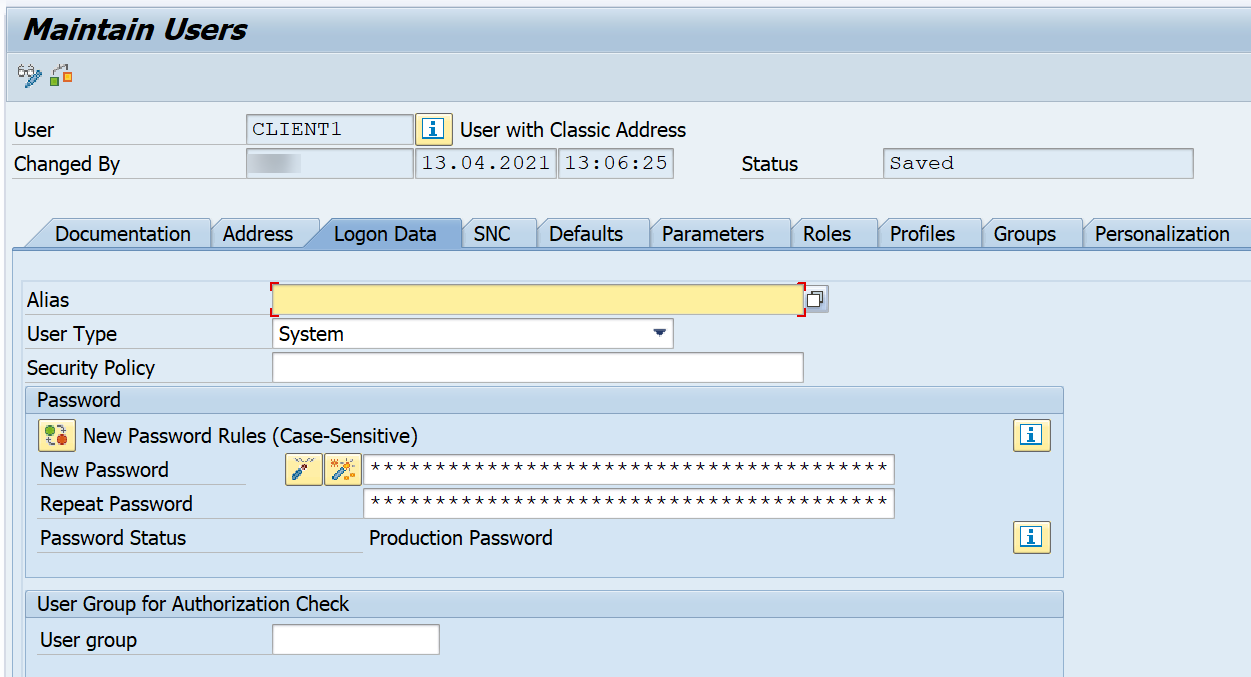
Step 3. Go to SU01 and create a system user that will be used for oAuth2 configuration. No roles or profiles are required to be assigned to this user.
Go to the transaction of /n/IWFND/MAINT_SERVICE, find service ZBOT_CENTRAL_SERVICE_SRV and enable oAuth for it:
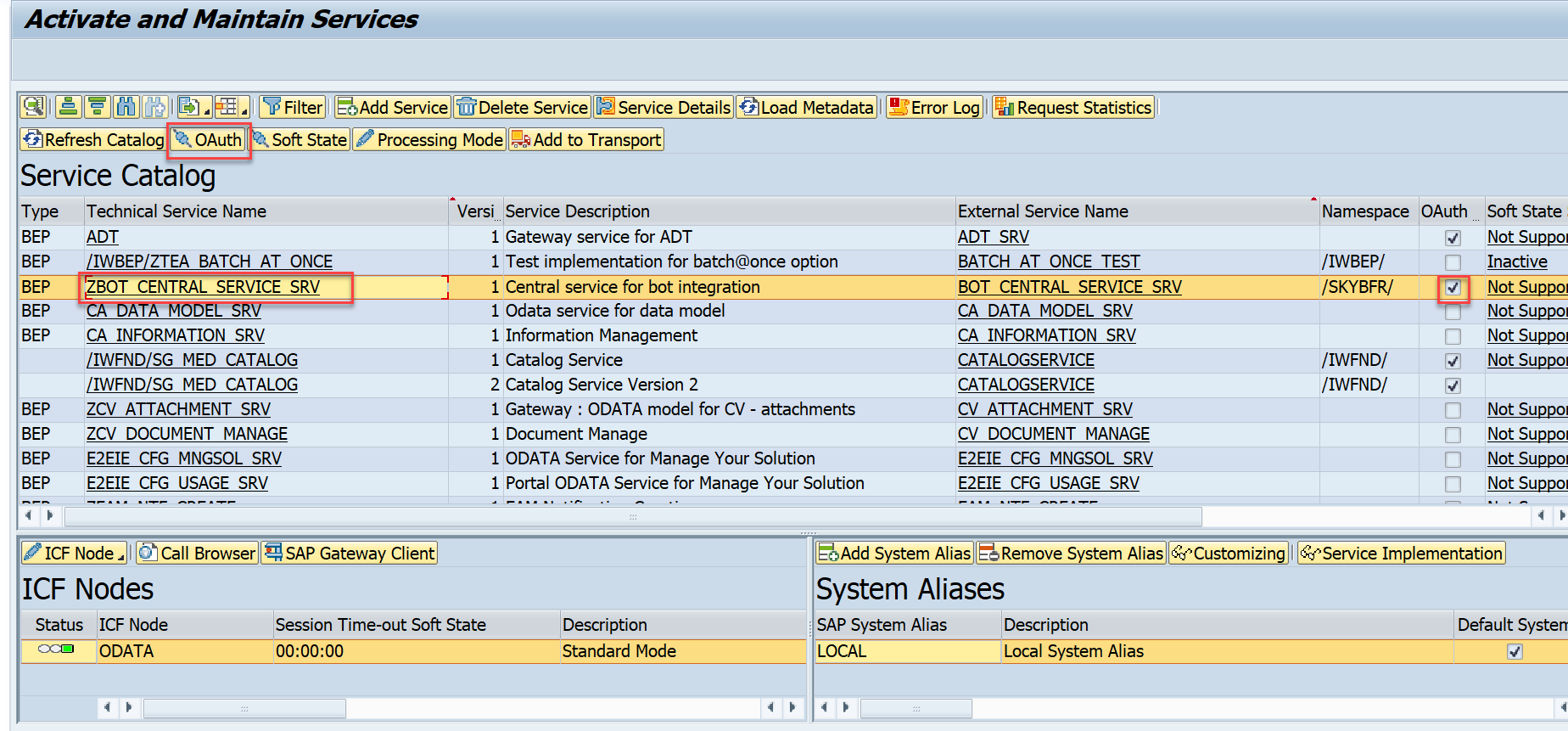
Step 4. go to the SOAUTH2 transaction and create a new client using the user ID created in the previous step.
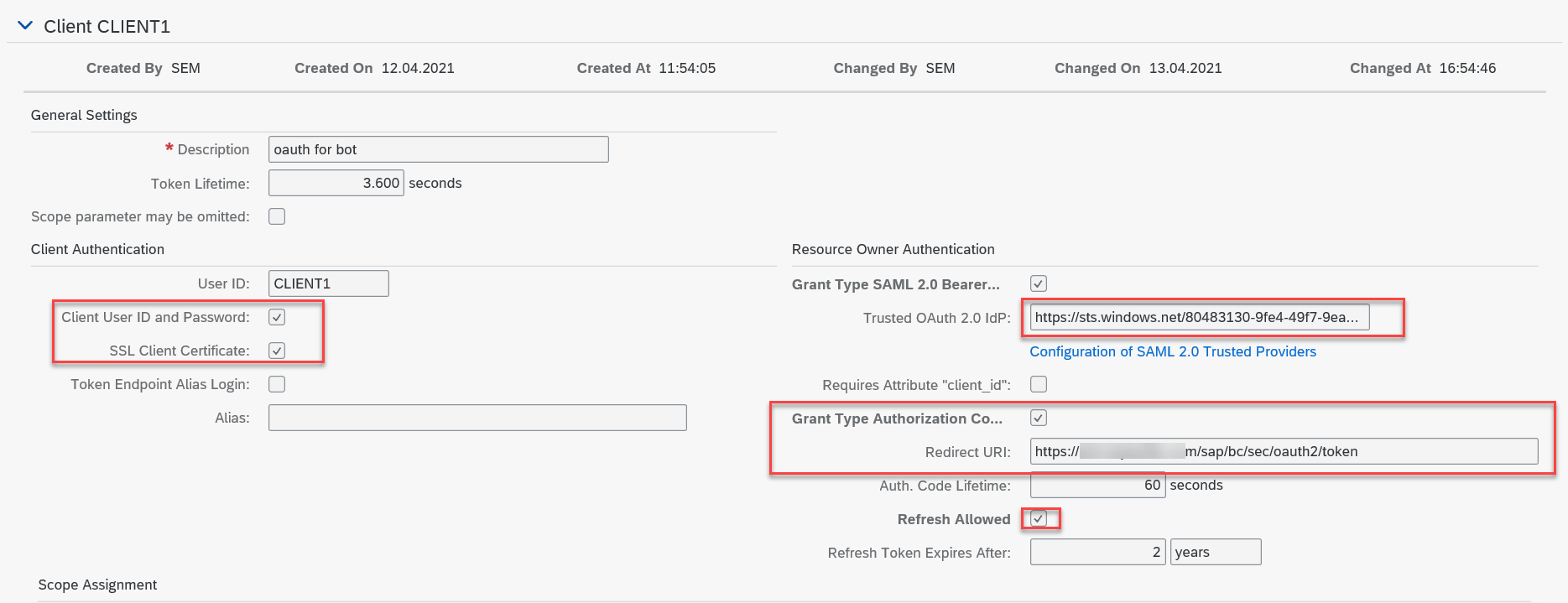
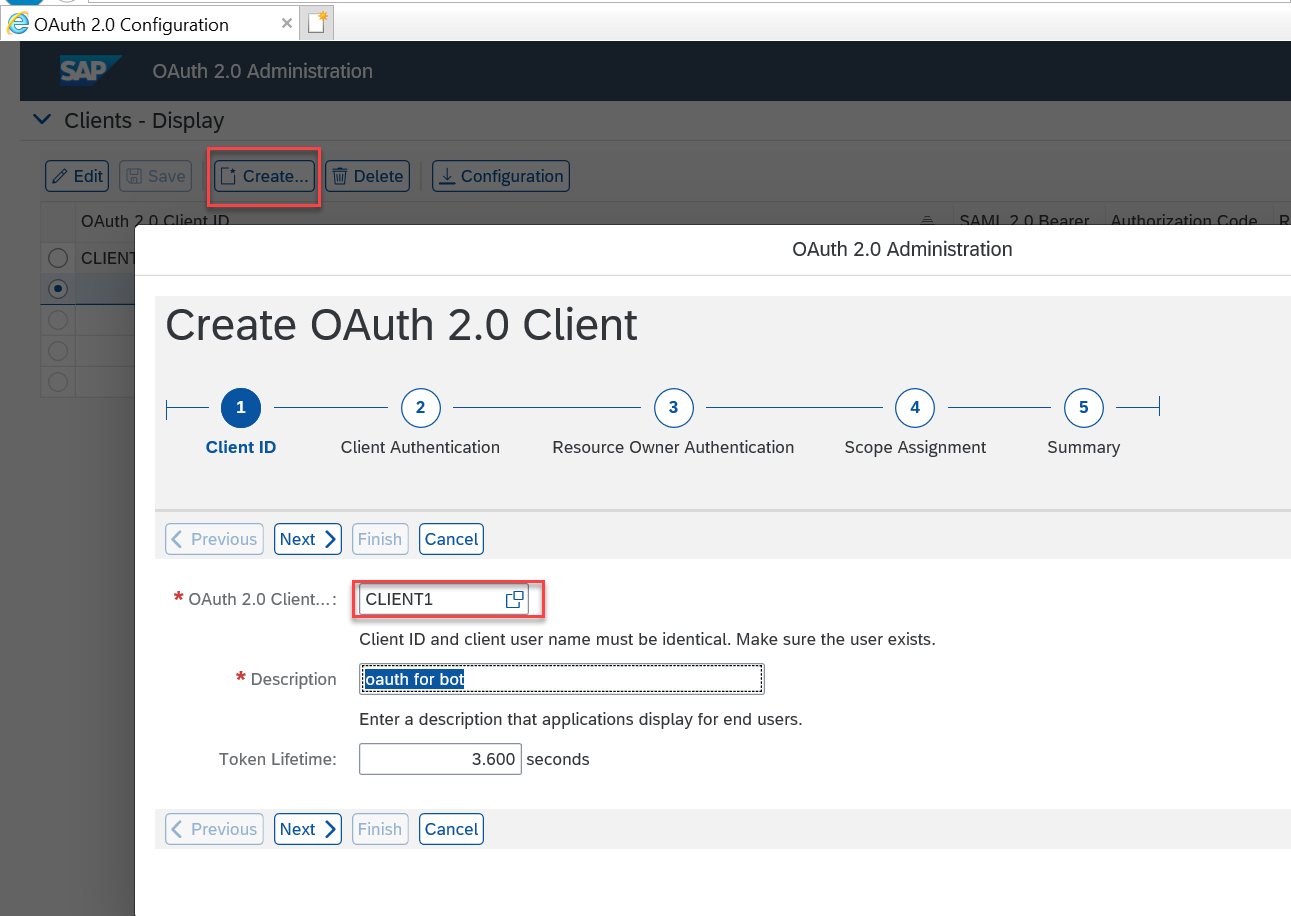
Maintain the settings as in the screen below
Step 5. For IdP, select the Trusted Provider created in the previous steps. For URL redirect, set https://<sap system hostname and port>/sap/bc/sec/oauth2/token
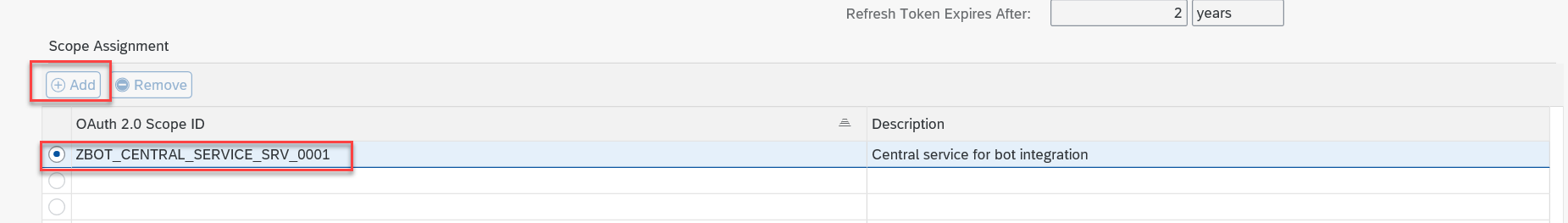
Next, add the scope for oData service ZBOT_CENTRAL_SERVICE_SRV
Paste the following values into the fields in SAP UI5 application:
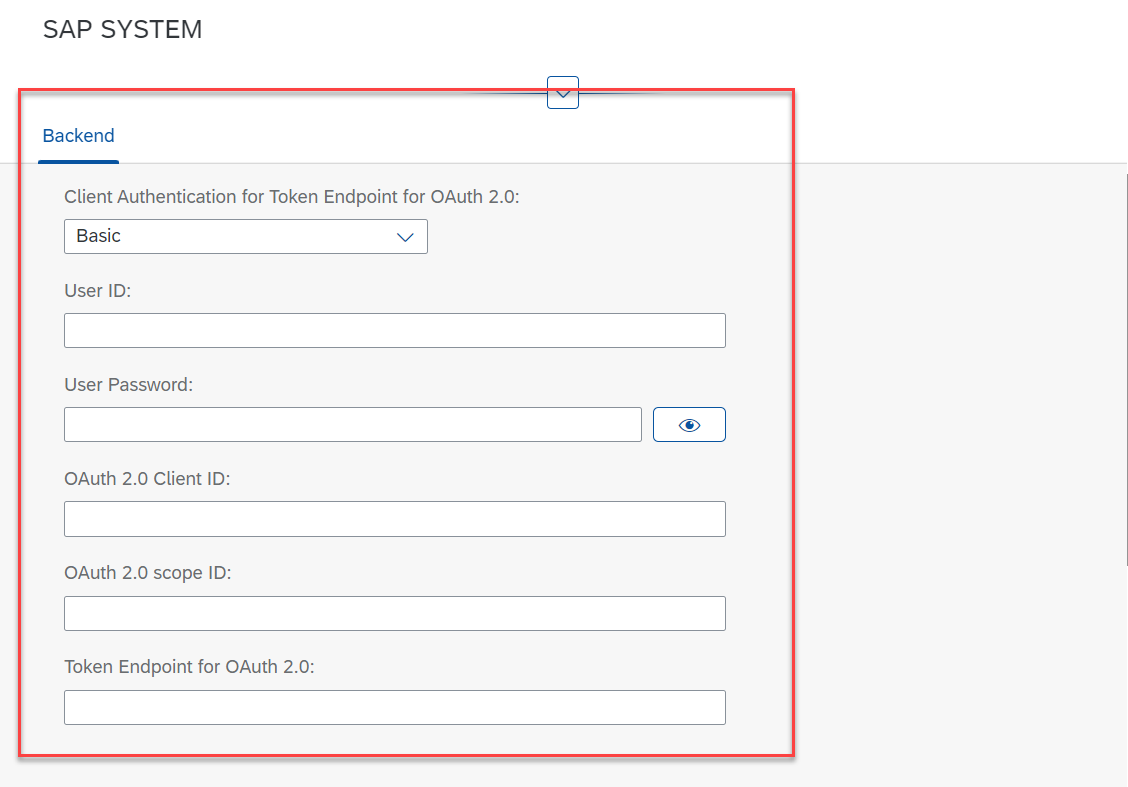
User ID and oAuth 2.0 client ID is the SAP user ID created for oAuth;
oAuth2 scope ID is typically ZBOT_CENTRAL_SERVICE_SRV_0001 (configured in this chapter above);
Token endpoint is typically https://<hostname and port of sap system>/sap/bc/sec/oauth2/token.
Step 6. Assign required authorizations to business users
In addition to OAuth2 technical configuration, business users must have the following authorization object assigned via their roles:
S_SCOPE:
OA2_CLIENT -> [OAUTH USER ID]
OA2_SCOPE -> [Central Bot Odata Service] (for example, ZBOT_CENTRAL_SERVICE_SRV_0001)
NOTE: Without this authorization, users will not be able to access the OAuth-protected OData service even if OAuth2 is configured correctly.
References: